January 22nd, 2016
How to Make Sure Your Legacy System is Secure
Many organizations have a legacy system that serve critical business needs. It’s important that they be assessed for security vulnerabilities.

Many organizations have a legacy system that serve critical business needs. It’s important that they be assessed for security vulnerabilities.
The strategy behind The Federal Data Center Consolidation Initiative (FDCCI) is to reduce cost, increase IT efficiency, and promote Green IT.
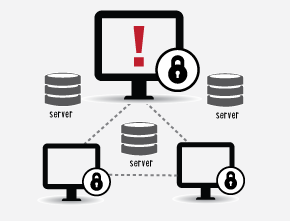
ACAS offers a more streamlined, centralized method for running scans, collecting scan data, and provides highly customizable reports.

Business and Government leaders met on August 8th at the 2013 AFCEA Bethesda Symposium to discuss mobile technology and strategies.

Security technical implantation guides, or STIGs, help DISA maintain the security posture of the DoD IT infrastructure. Learn more about it here.