Blogs
-
 April 30th, 2014
April 30th, 2014The SQL Server PIVOT Query
MoreThe PIVOT operator in SQL Server is used to rotate your query output 90 degrees so the unique column values can be transposed to column headers.
-
 April 28th, 2014
April 28th, 2014What Do the Android Permissions Mean?
MoreFind out what the Android permissions are and how you can protect yourself when downloading mobile apps in Google Play and on the Amazon Marketplace.
-
 April 24th, 2014
April 24th, 2014Why Should I Redesign My Website?
MoreEven if your website is functionally up to date, consider a periodic redesign to maintain a modern look and feel and meet current standards for usability.
-
 April 11th, 2014
April 11th, 2014Heartbleed Bug: Increasing Awareness of Information System Security
MoreProtect yourself from vulnerabilities like Heartbleed by not using the same password, increasing the difficulty of security questions & remaining vigilant.
-
 April 11th, 2014
April 11th, 2014What’s the Heartbleed Bug and How Can You Protect Yourself?
MoreThe Heartbleed bug is a pretty serious vulnerability inside OpenSSL. Systems Adminstrator Jeremy Rochon offers his tips for protecting yourself.
-
 April 4th, 2014
April 4th, 2014What Are Infographics and When Should You Use Them?
MoreInfographics are a form of data visualization and are frequently used for teaching, inspiring, and communicating a lot of information in a graphical format.
-
 April 3rd, 2014
April 3rd, 2014How to Survive the Technical Interview
MoreSoftware Engineer Kevin Benore discusses what you need to know when facing a technical interview for a job in the IT field.
-
 March 31st, 2014
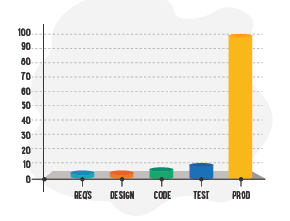
March 31st, 2014The Rising Costs of Defects
MoreImplementing quality control reviews earlier in your development process to detect defects will lower your overall project cost.
-
 March 28th, 2014
March 28th, 2014The Impact of Code Quality on Test Coverage Planning
MoreThe degree of test coverage that can be provided by software project testing will be shaped and constrained by available project resources and code quality.
-
 March 27th, 2014
March 27th, 2014What’s New in Windows Server 2012 R2?
MoreWindows Server 2012 R2 provides several new features and improvements over previous versions. Learn about the new offerings here.
-
 March 25th, 2014
March 25th, 2014Top 5 Reasons Your Legislative Conference Needs a Mobile App
MoreIf you’re hosting a legislative conference, you should have a mobile app for your event because it provides attendees with everything they need to know.
-
 March 21st, 2014
March 21st, 2014Proper Password Persistence
MoreProper password persistence is essential and may include the usage of a crytographic hash, a salt value, or password based key derivation functions.