The Department of Defense (DoD) has implemented many different processes to manage information assurance (IA) measures in an effort to protect their assets. DoD IA professionals are well aware that these policy changes occur often and usually require updates to their respective systems in order to keep them compliant. Because of the way networks are currently integrated between organizations and other non-DoD agencies, certain challenges arise when groups use different processes to manage risk while effectively securing their systems. The current DoD Information Assurance Certification and Accreditation Process (DIACAP) improved on system integration challenges within the DoD, but there’s been direction to broaden this exposure to include other Federal government agencies while focusing on the management of organizational risk.
To address this, along with other issues, the DoD formed the Joint Task Force Transformation Initiative Interagency Working Group to align their IA programs with the Federal government’s risk management policies. The group includes representatives from the National Institute of Standards and Technology (NIST), DoD, Committee on National Security Systems (CNSS), and the Office of the Director of National Intelligence (ODNI). NIST and CNSS already provide an extensive, all-encompassing approach in managing risk known as Risk Management Framework (RMF) and while the DoD participates in the development process, they primarily leverage NIST/CNSS approaches to meet DoD needs.
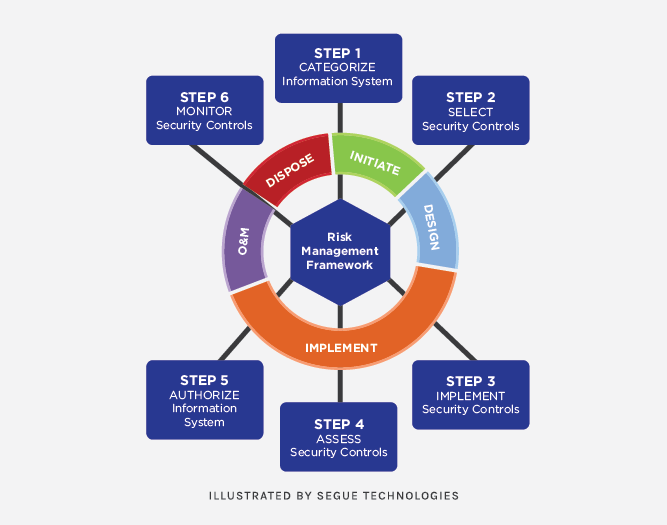
DoD IA professionals will notice several differences when moving from DIACAP to RMF. They include changes in roles and responsibilities, processes, and of course, lexicons. In DIACAP, systems are typically assigned a single Designated Approving Authority (DAA) or perhaps an alternate DAA Representative. RMF will not only replace the DAA with an Authorizing Official (AO), but implements joint authorization, meaning multiple officials from within or outside the primary organization will share responsibility for authorizing and accepting system-related security risks. Another difference is the traditionally used C&A (Certification & Authorization) process being replaced with A&A (Assessment & Authorization). While the primary focus of the process (technical and non-technical system evaluation) will remain the same, A&A does introduce a new lifecycle process that integrates security and risk management activities into the System Development Life Cycle. NIST SP 800-37, Guide for Applying the Risk Management Framework to Federal Systems, demonstrates this process in six major steps:
- Categorize Information System
- Select IA Controls (based of categorization in Step 1)
- Implement IA Controls
- Assess IA Controls
- Authorize Information System
- Monitor IA Controls
Probably the most significant difference will be the transition from the DIACAP DODI 8500.2 IA controls to the RMF’s NIST SP 800-53 Revision 4 standard control set. RMF implements a more complex, three-dimensional matrix formula for assigning a combination IA controls to specific systems.
The Air Force has already updated several of their IA policies and guidance to include RMF strategies to better align their processes with the goal of creating a unified information security framework that will provide benefits at multiple levels. AFI 33-200, Cybersecurity Programs, and AFI 33-210, AF Assessment and Authorization Program, are just two instructions that are targeted for final coordination by the 4th quarter of FY15. From CIOs and system owners to warfighters and developers, this new standardized approach looks to improve on cost savings, rapid solution deployments, greater interoperability between components, more consistent data, and better coordination and integration of security in the development and acquisition processes. Increased savings and tighter security are debatable topics, but any IA professional will agree that any effort to streamline the process for all agencies would provide a huge boost in efficiency when it comes to systems development and migrations.
While the DoD has directed all components to transition to RMF by FY17, the Air Force has a “Go Do” Message tentatively scheduled for the 4th quarter of FY15. The last ATO package to be submitted under DIACAP will be during the 1st quarter of FY17. The latest ATO expiration date under DIACAP will be sometime during the 3rd and 4th quarters of FY18. This timeline should provide enough time for officials to resolve any current gaps and concerns relating to strategy, manpower, or training. IA practitioners are urged to begin preparing for the transition now as more information and updates are released. Vendors are already providing courses to enhance RMF life cycle skills and knowledge of NIST/CNSS IA control guidelines. A comprehensive training plan and leadership support at all levels across the DoD will be key to ensuring a successful transition.
Segue Technologies® has maintained a solid presence in the developing and management of IA profiles for numerous DoD systems. Our extensive experience in systems development, network engineering and security provides the toolset necessary to quickly adjust with any shift in the DoD and Federal IA landscape. Find out more about custom web application development services.